APIs are synonymous with applications. Modern Application Security is largely about securing your APIs, as they are the mechanism via which users interact with your applications.
APIs serve as a critical conduit for data flow between users and applications.
Too often developers perceive Application/API Security as a dark and complicated art. Application security seems to be a mysterious black box, resulting in a tenuous relationship between Developers and Security teams.
The crux of this is an education and awareness issue. Developers operate based on principles and causation, and often security is thrust upon them without providing the proper big picture context.
Getting a grasp of these four foundational concepts will greatly simplify your API security journey, and make adopting and implementing application security much easier.
1. Don’t Blindly Trust External Inputs

APIs have a defined JSON schema, and accept inputs from clients. Often a lot of API security vulnerabilities arise from blindly using these inputs without validating or sanitizing them.
Common vulnerabilities from the lack of input validation are Injection, Denial of Service, and Mass Assignment.
Always check if the input data provided is within the expected constraints for your API endpoint. Parse the input data and enforce minimum/maximum range, string length limits, data type formats, etc.
2. Enforce Authentication for APIs Requiring User Identity

Suboptimal authentication mechanisms lead to unauthorized access to privileged APIs. Distinguish between API endpoints that don’t require any user identity (anonymous API endpoints) and those which require user identity (authenticated API endpoints).
Since user identity is established only after authentication, always enforce proper authentication for API endpoints that require knowledge of the user’s identity.
3. Implement Granular User Access Controls (Authorization)
APIs are highly susceptible to Horizontal Authorization and Vertical Authorization exploits, resulting in customer data leakage.
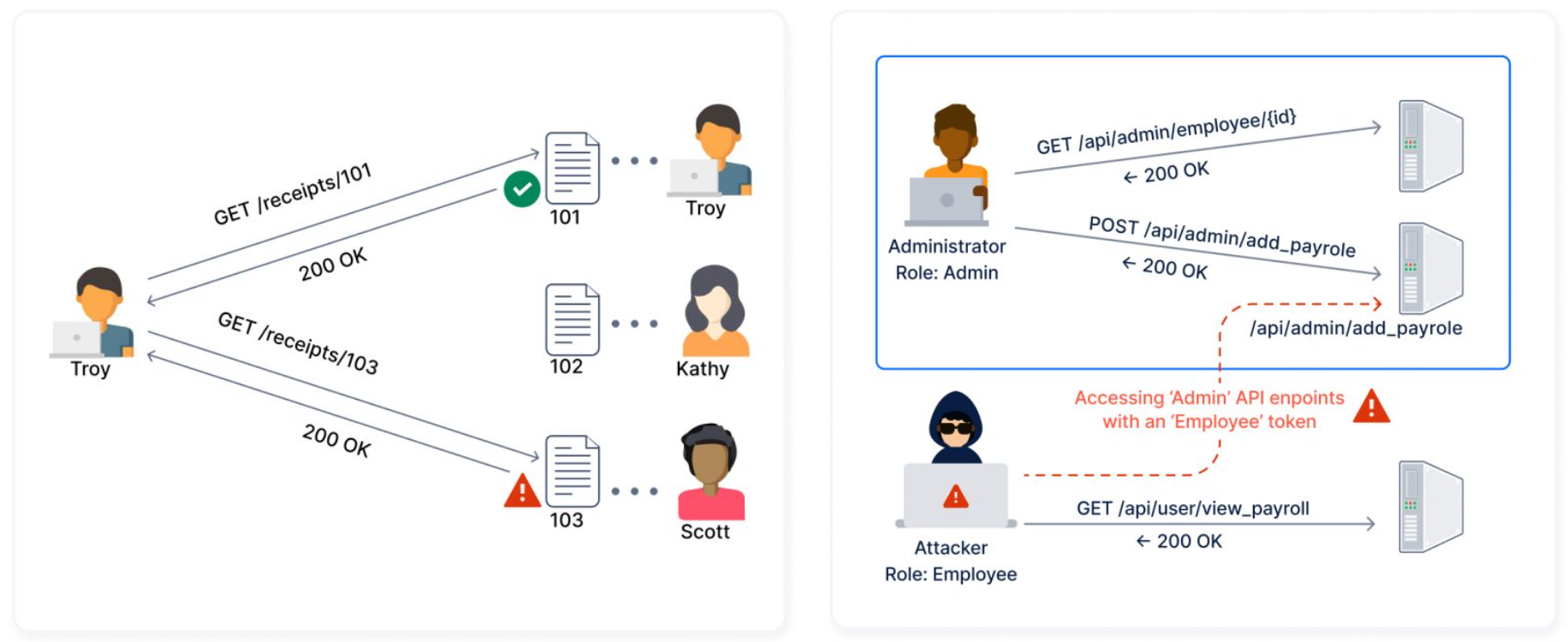
Do not blindly service API requests from authenticated (logged in) users. Always check if the specific resource requested by the authenticated user, actually belongs to the user, and/or if the user has specific access rights for the resource.
4. Implement Granular Service Access Controls (Authentication/Authorization)

Modern applications are built using a pattern called Microservices Architecture (MSA), which connects numerous small-sized services together using APIs.
In this pattern, there is no traditional network perimeter and no clear delineation between external-facing services and internal-only services. All services and their APIs are considered to be externally accessible.
In such architectures it is important to do the following:
a. Authenticate every API call to the service, even if the API call is from another microservice that you trust (because you own it).
b. Check if the requesting service is allowed to make the specific request (caller service has business justification to talk to the callee service), and if the requested resource should be accessible by the caller service.
Now that the concepts are clear and API security is not a big mystery, you can move to adopt these concepts in your application on a daily basis.
Levo is a purpose-built, developer-first API security solution that provides full validation of the aforementioned concepts in your API implementation.
Levo auto generates security validation tests that are run, in a self-serve manner similar to unit and integration tests, that run in CI/CD pipelines.
Signup for a forever-free plan here, and start building secure and resilient APIs in minutes.
Thanks for reading,
Harish