As a former engineering leader, I know the pressure you face to accelerate deployment without sacrificing security.
Speed is essential—faster releases push business goals forward. But as deployment rates climb, manual security checks can’t keep up, leaving your applications vulnerable.
This challenge becomes even more critical when sensitive data—like credit card numbers, addresses, PII, or PHI—flows through your APIs.
Then, a breach doesn’t just mean downtime; it means exposing customer data, where business objectives quickly derail.
Nearly half of consumers stop buying from companies they don’t trust with their privacy, and compliance violations only compound the damage.
For fintech, the stakes are even higher. PCI fines can reach $10,000 monthly until issues are resolved, and every lost PII record can cost $180.
This blog discusses achieving compliance success despite a high deployment rate.
APIs and Sensitive Data: A strong yet imperfect match
APIs are the backbone of data exchange between clients and databases, handling everything from user information to sensitive data like credit card numbers and healthcare details. Given this role, most compliance schemes—whether PCI DSS, HIPAA, or GDPR—now mandate a comprehensive inventory of APIs and a classification of the sensitive data they manage.
However, protecting and detecting these sensitive data flows is no small feat, as evidenced by the 31% of enterprises that reported sensitive data exposure in their production APIs.
For fintech companies, for example, PCI compliance requires strict protection of cardholder data. This means tracking API calls and mapping the flow of sensitive information across networks.
With the PCI DSS Phase 2 deadline approaching in March 2025, enterprises have just two quarters to meet foundational requirements like securing cardholder data, enforcing role-based access, and monitoring encryption, all of which hinge on finding APIs that handle sensitive data.
Now, imagine trying to handle this manually.
Your InfoSec engineers would need to gather a complete API inventory, reaching out to every development team for details on the APIs they’ve worked on—most of which won’t be readily available.
In fact, 75% of enterprises report not having a complete API inventory.
Even if they collect some data, it’s unlikely to cover all environments or APIs.
Engineers would then have to sift through this incomplete information to determine which APIs are handling sensitive data, what kind of data is flowing, and whether the proper security controls are in place.
All this while API sprawl continues to grow—27% of enterprises doubled their API count in 2023 compared to 2021.
A lack of API inventory is a massive problem, but it’s just the tip of the iceberg. Detecting sensitive data flows across APIs is even more complex due to these issues:
Given these hurdles, with PCI DSS Phase 2 less than six months away, your DevSecOps team likely doesn’t have the bandwidth or time to handle this manually. Automating the detection of sensitive data flows is the only scalable solution.
Automated API Security Platform Levo.ai
Our platform streamlines the entire sensitive data detection and API inventory process by automating the tedious tasks your team would otherwise struggle with:
- Comprehensive API Inventory: We leverage your traffic and code repositories to build the complete API inventory, including internal, external, open-source, third-party, and even inactive APIs like zombie and shadow APIs—uncovering 90-250% more APIs than you were aware.
- Automatic API Documentation: We generate thorough API documentation through OpenAPI/Swagger specifications, complete with over 12 critical parameters such as version details, changelog, and request-response bodies.
- Sensitive Data Mapping: Our platform automatically detects and maps all sensitive data flows through your APIs, even across third-party and partner services, ensuring no blind spots.
- Security Gap Identification: We identify endpoints handling sensitive data with no or weak authentication, allowing you to address vulnerabilities before they become threats to your customers and brand.
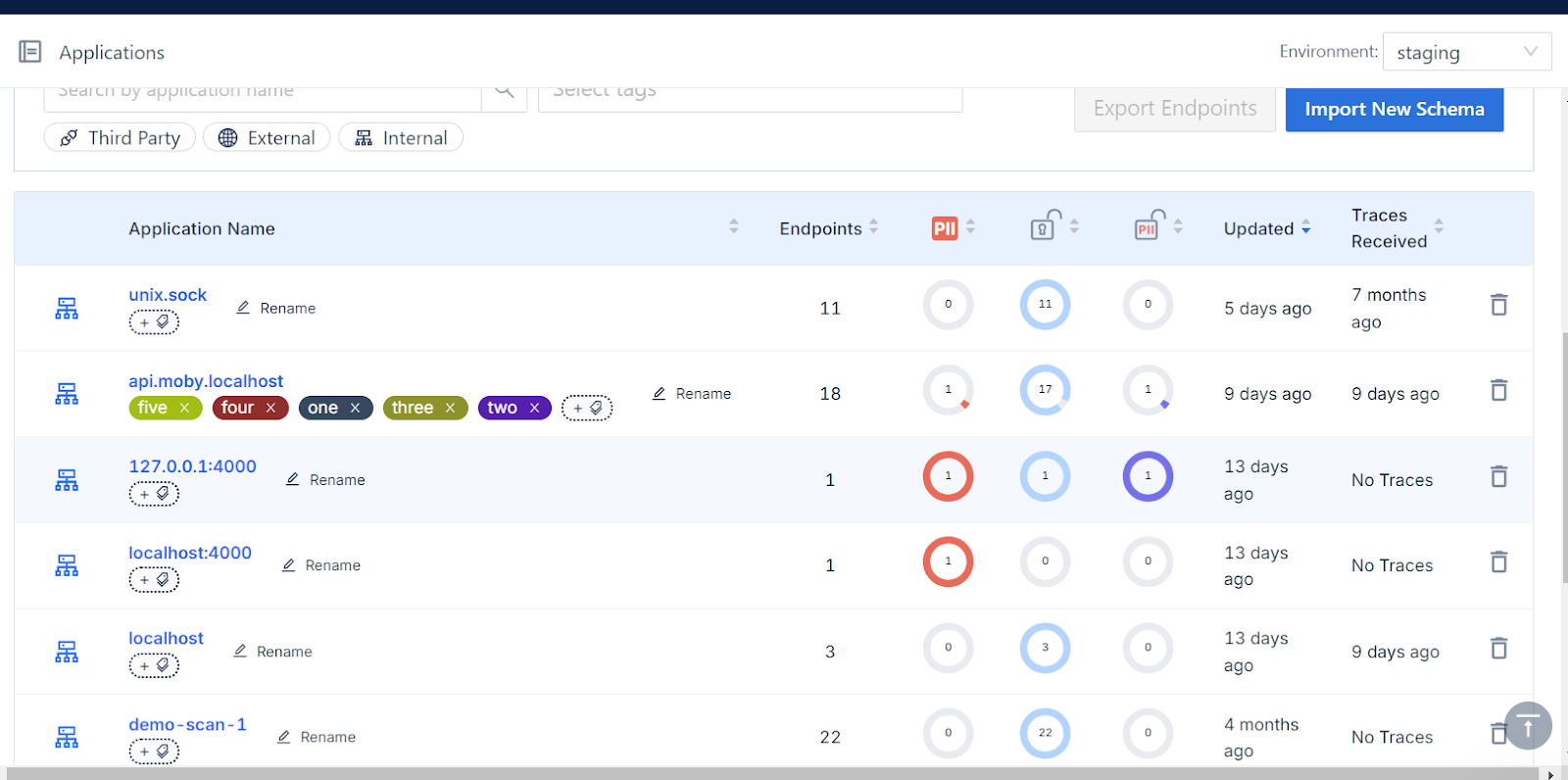
- Flexible Data Tracking: All sensitive data types are mapped at both the application and environment levels, with the added flexibility to define new data types directly through the UI.
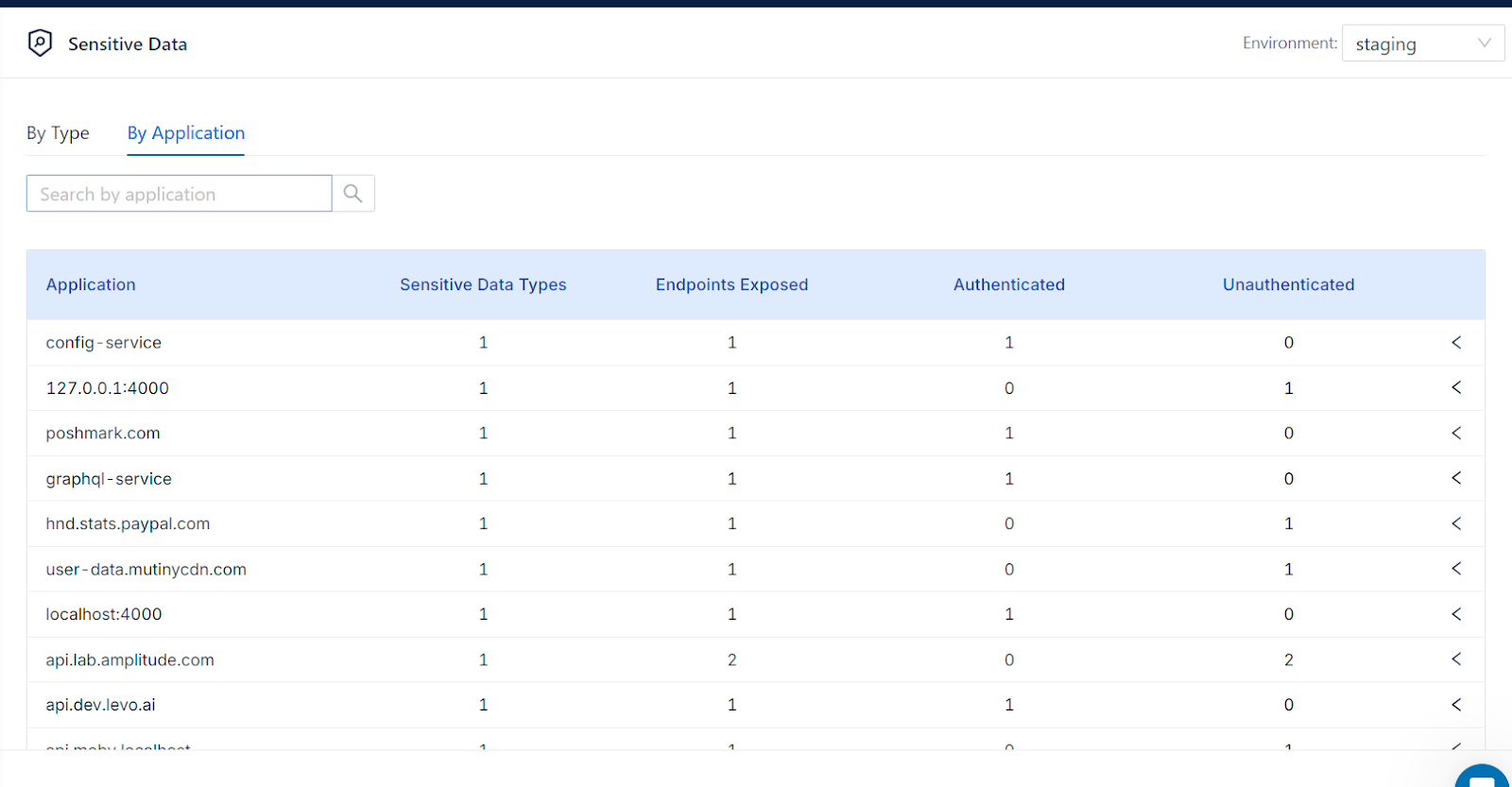
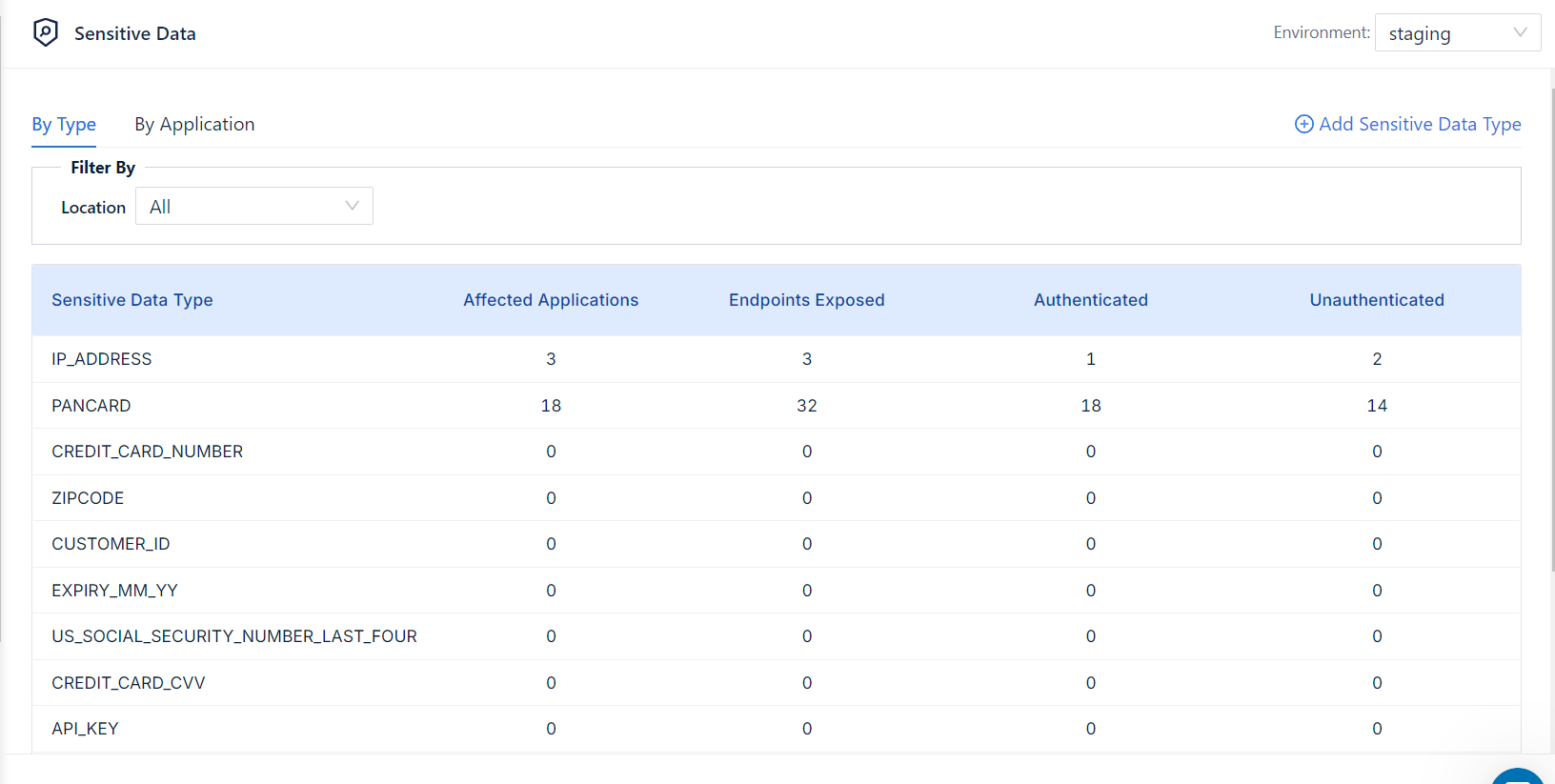
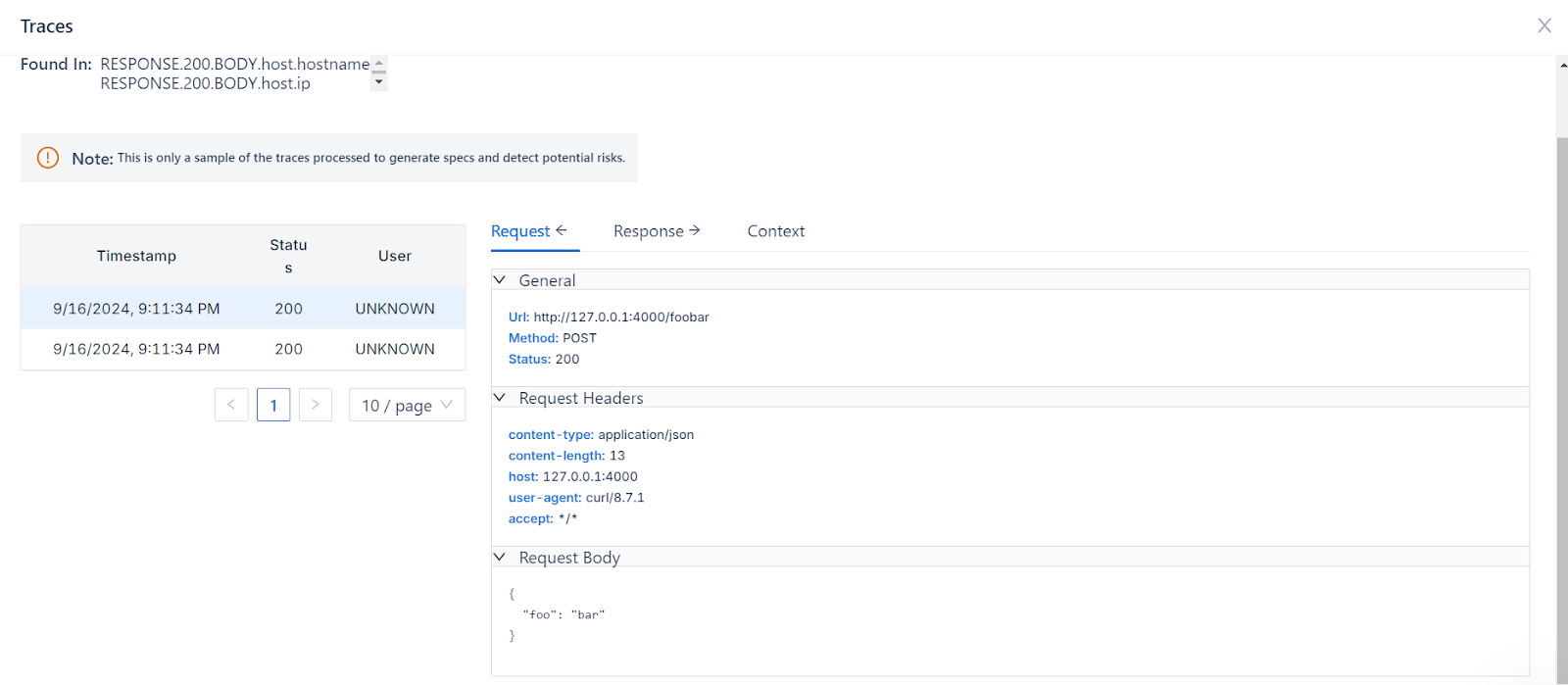
Our trace-linking capability ensures that the data flows we detect are accurate and contain actual sensitive data rather than false positives. With your permission, we collect traces and surface them alongside sensitive data, providing you with unparalleled visibility and control.
Book a demo through this link to see this live in action!

.svg)






.jpg)
